ExtremeXOS Operating System Version 12.6
For Highly Available, Extensible, High-performance Networks

Overview:
Extreme Networks has created the ExtremeXOS modular Operating System (OS) – for highly available, extensible, high-performance networks. ExtremeXOS high availability architecture with EAPS protocol helps reduce network downtime for business continuity and access to mission-critical applications such as CRM, data warehouses and VoIP for carrier and voice grade networks.
Built-in security capabilities provide network access control integrated with endpoint integrity checking, identity management, and protection for the network control and management planes.
With ExtremeXOS you can extend the capabilities of your network by integrating specialized application appliances such as security devices into the network, providing insight and control at the network, application and user level.
Highlights
ExtremeXOS has a robust set of Layer 2 and Layer 3 control protocols, provides a flexible architecture for highly resilient networks and has been designed to support the next-generation Internet Protocol, IPv6. ExtremeXOS is a highly available and extensible software foundation for converged networks. ExtremeXOS offers high availability for carriergrade voice and video services over IP and for supporting mission-critical business applications such as CRM.
- Modular Operating System
- High Availability Architecture
- Rich set of Layer-2 and Layer-3 protocols and features
- Secure Management
- Extensibility
- Integrated Security with NetLogin, MAC Security, IP Security
- User, location, and time-based dynamic security policies with Identity Management
- Insight, control and automation for virtualized data centers with XNV (ExtremeXOS Network Virtualization)
- Enhanced resiliency, synchronization, performance for 2G/3G/4G mobile backhaul
- ExtremeXOS InSite SDK
- Software Defined Networking Ready with OpenFlow and OpenStack support
- Ethernet Audio Video Bridging (AVB) enabled
Architectural Highlights
- Memory protection for processes
- Self-healing process recovery via process restart or hitless failover
- Dynamic loading of new functionality
- Scriptable CLI for automation and event-triggered actions
- XML open APIs for integrating third-party applications
- Dual-stack IPv4 and IPv6 support
High Availability Architecture
- Reduce network downtime using hitless failover and module-level software upgrade
- Prevent system corruption using memory protection for processes
- Avoid system reboots using self-healing process recovery
- Extend high availability across switches with Multi-Switch Link Aggregation Groups
Extensibility
- Integrate best-of-breed applications to your network with an open, yet secure XML-based Application Programming Interface (API)
- Integrate Extreme Networks and third-party developed software applications using open standards-based POSIX interfaces
- Scripting-based device management for incremental configuration deployment and ease of management
Integrated Security
- Guard access to the network through authentication, Network Login/802.1x, host integrity checking, and Identity Management
- Harden the network infrastructure with Denial of Service(DoS) protection and IP Security against man-in-the-middle and DoS attacks
- Secure management using authentication and encryption
Features:
High Availability
Modular Operating System
Preemptive scheduling and memory protection allow each of many applications – such as Open Shortest Path First (OSPF) and Spanning Tree Protocol (STP) – to run as separate OS processes that are protected from each other. This provides increased system integrity and inherently helps protect against DoS attacks.
ExtremeXOS offers high network availability using process monitoring and restart.
The modular design of ExtremeXOS allows the upgrading of certain individual software modules, should this be necessary, leading to higher availability in the network (see Figure 1). This includes security stacks such as SSH and SSL.
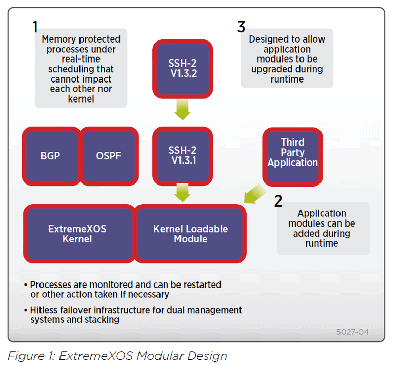
Hitless Failover and Graceful Restart
With dual management modules on BlackDiamond chassis systems and advanced stacking support with Summit fixed-configuration switches, ExtremeXOS is capable of preserving the state of resiliency and security protocols such as STP, EAPS and Network Login, thus allowing hitless failover between management modules/redundant masters in case a module or master fails.
Graceful restart is a way for OSPF-2, BGP-4 and IS-IS protocols to restart without disrupting traffic forwarding. Without graceful restart, adjacent routers will assume that information previously received from the restarting router is stale and it won’t be used to forward traffic to that router. If the peer routers support the graceful restart extensions, then the router can restart the routing protocol and continue to forward traffic correctly.
If the network topology is not changing, the static routing table remains correct. In most cases, networks can remain stable (i.e. would not re-converge) during the time for restarting OSPF, BGP or IS-IS. Should route updates still exist, graceful restart incrementally performs these updates after the restart.
CPU Denial of Service Protection
A DoS attack is an explicit attempt by an attacker to degrade or disable a switch by overwhelming the switch’s system resources. ExtremeXOS CPU DoS protection helps prevent attacks from crippling the Extreme Networks switch. This ExtremeXOS capability can detect, analyze and respond to threats directed at the switch CPU.
Extensibility
Dynamic Module Loading
ExtremeXOS provides an infrastructure to dynamically load, start and gracefully stop new applications. ExtremeXOS embraces POSIX-compliant interfaces that ease the integration of new applications. ExtremeXOS uses this infrastructure to dynamically load Extreme Networks developed functionality such as SSH/SCP/SSL that is export-controlled, avoiding the requirement for new operating system image installs to gain this functionality. The same infrastructure is also used to integrate third-party developed applications. An example is a VoIP application layer monitoring agent developed to simulate and closely monitor VoIP connection behavior in a network.
Scripting
ExtremeXOS provides a CLI scripting infrastructure through Python or Tcl languages. Scripting can be used to add incremental configuration to the network infrastructure, such as a list of VLANs to be configured. This capability eases the roll-out of networks, reduces repetitive tasks and configuration errors. Scripting capabilities, such as system-and user-defined environment variables, such as if/then and loops, allow automating regular management tasks in scripts and deploying configurations such as QoS, rate limiting and ACLs, for example, to multiple ports. Scripts can access CLI output, and a rich set of Python or Tcl functions that provide a utility library of string manipulation, search or mathematical functions. By leveraging scripting for switch configuration, rolling out a new switch can be reduced to minutes and just a few commands for switch-specific settings. Scripting is also used in the ExtremeXOS Universal Port framework to define trigger event actions.
XML Application Programming Interfaces
Extreme Networks uses XML APIs – concepts originally developed in the emerging field of Web services. ExtremeXOS can provide a secure, simple mechanism to access processes and information within the switch. For example, a security appliance can utilize ExtremeXOS to limit access, control bandwidth or redirect traffic from a client that is attempting to connect to the network. XML also provides a scalable and reliable transport for device configuration and statistics, for example OSS and service provisioning systems in Carrier Ethernet deployments.
This XML infrastructure embraces the concept of open yet secure communications to allow business applications to easily interact with the network for security policy enforcement, regulatory compliance and performance management, and higher security.
The XML infrastructure is also used by ExtremeXOS ScreenPlay™ Web-based management interface.
Ease of Management
Link Layer Discovery Protocol (LLDP, IEEE 802.1AB)
ExtremeXOS support of IEEE 802.1ab standards-based discovery protocol provides vendor-independent device discovery as well as integration with VoIP infrastructure and phones, including E911 ECS location, inventory information, PoE budgeting and configuration of information such as VLANs and QoS tagging.
LLDP not only simplifies deployment and locating of access devices, but it can also be used as a troubleshooting and firmware management tool.
LLDP is tightly integrated with the IEEE 802.1x authentication at edge ports. As endpoint devices are first authenticated, the LLDP-provided information is trustable and can be used for automated configuration, helping protect the network from attacks against automated configuration mechanisms.
Network Traffic Monitoring
ExtremeXOS sFlow and IPFIX standards-based data monitoring support provides Layer 2-7 visibility into the network, including statistics on which applications are running over your network, biggest talkers, etc.
sFlow is a sampling technology that meets the key requirements for a network traffic monitoring solution: sFlow provides a network-wide view of usage and active routes. It is a scalable technique for measuring network traffic, and collecting, storing and analyzing traffic data. This enables thousands of interfaces to be monitored from a single location.
sFlow is scalable, thereby enabling it to monitor links of speeds up to 10 Gigabits per Second (Gbps) and beyond without impacting the performance even of core Internet routers and switches, and without adding significant network load.
IPFIX (Internet Protocol Flow Information eXport), or RFC 3917, can be used as an alternative to sFlow. IPFIX offers templates for the data to be transferred, or network managers can define data types to adapt to their specific needs.
Universal Port
ExtremeXOS Universal Port infrastructure is a powerful framework of event-driven activation of CLI scripts. While Universal Port can leverage any system event log message as an event trigger, the most popular use cases are time/user/location-based dynamic security policies as well as VoIP auto-configuration. For these applications, Universal Port uses standards authentication (Network Login/802.1x) and discovery protocols (LLDP + LLDPMED) as trigger events. Actions in the form of fully configurable CLI scripts can be tied to events on a per-port basis. As such, dynamic security policies, including fine-grained access control via ACLs, can follow a user independently of where he logs into the network. VoIP phones and the connecting switch edge port can be auto-configured for the voice VLAN and QoS. The switch can receive the exact, fine-grained power budget requirements from the phone and provision it accordingly. The phone can receive the E911 ECS location from the switch as well as the call server address in order to receive additional configuration. Deploying VoIP endpoints is as easy as opening the package, programming the extension and plugging into the network. The following diagram explains the mechanism. Please note that steps 1 and 2 are only done once, using scripting, and then rolled out to all voice-capable ports. Steps 3 to 5 are the resulting automatic runtime events.
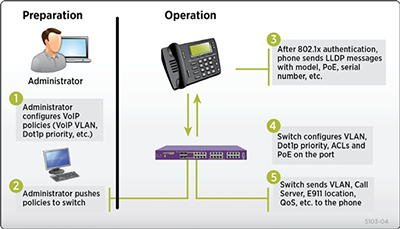 Figure 2: VoIP Auto Configuration with ExtremeXOS Universal Port
Figure 2: VoIP Auto Configuration with ExtremeXOS Universal Port
Integrated Security
Network Login
Extreme Networks open, standards-based approach allows network access control on all edge ports of a network. Access control works with or without dedicated authentication support on client devices, such as VoIP phones and printers.
Network Login enforces authentication before granting access to the network.
ExtremeXOS Network Login supports multiple supplicants on the same switch edge port, even in separate VLANs. For example, a VoIP phone can be authenticated into the voice VLAN, and a PC connected to the data port of the phone can be authenticated into a user-specific VLAN.
Network Login supports three methods: 802.1x, Web-based and MAC-based. All methods can be enabled individuallyor together to provide smooth implementation of a secured network.
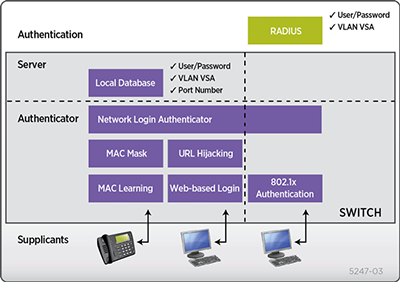 Figure 3: Network Login
Figure 3: Network Login
Integrated Security
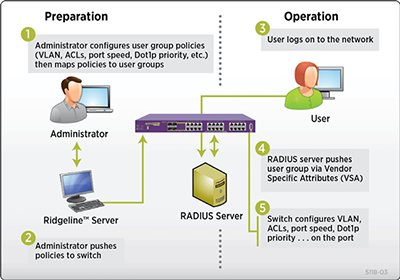
Dynamic security policies can be deployed via RADIUS Vendor Specific Attributes (VSAs). As an example, the VLAN for a given user or device can be dynamically assigned. Network Login optionally will dynamically create the VLAN if it does not exist on the edge switch, dramatically reducing the burden of managing VLANs. In Extreme Networks implementation, leveraging the fully configurable ExtremeXOS Universal Port infrastructure, dynamic security policies including VLAN assignments (see Figure 4).
Dynamic policies may also include rate limiting, QoS and dynamic ACLs. Dynamic security policies are activated and deactivated based on authentication and hosts connecting or disconnecting from the network. As the actual implementation of the policy can be changed from port to port, the framework allows for location-based policies. Integration with a timer event provides time-based policies, such as disabling wireless access after business hours.
MAC Security
MAC Security allows the lockdown of a port to a given MAC address and limiting the number of MAC addresses on a port. This can be used to dedicate ports to specific hosts or devices such as VoIP phones or printers and avoid abuse of the port. In addition, an aging timer can be configured for the MAC lockdown, protecting the network from the effects of attacks using (often rapidly) changing MAC addresses.
IP Security
The ExtremeXOS IP security framework protects the network infrastructure, network services such as DHCP and DNS and even host computers from spoofing and man-in-the-middle attacks. It also provides network protection from statically configured and/or spoofed IP addresses as well as building an external trusted database of MAC/IP/port bindings so that you always know where traffic from a specific address comes from for immediate defense.
Identity Manager
Identity Manager allows network managers to track users who access their network. User identity is captured based on NetLogin authentication, LLDP discovery and Kerberos snooping. ExtremeXOS uses the information to then report on the MAC, VLAN, computer hostname, and port location of the user. Further, Identity Manager can create both roles and policies, and then bind them together to create role-based profiles based on organizational structure or other logical groupings, and apply them across multiple users to allow appropriate access to network resources.
In addition, support for Wide Key ACLs further improves security by going beyond source/destination and MAC address as identification criteria to examine the IP address and VLAN of the user as well.
Secure Management
ExtremeXOS provides secure management via SSH2/SCP2/SSL and SNMPv3, providing authentication and protection against replay attacks, as well as data privacy via encryption.
Access profiles for device management allow filters to be set on device management, accepting connections only from specified sources.
CPU DoS Protect throttles traffic directed to the switch and can automatically set an ACL for defense, thus protecting the switch from the effects of DoS attacks such as “Ping of Death” and others. This defense mechanism works for all CPU bound traffic – Layer 2, IPv4 and IPv6.
Routing protocols such as OSPF-2 and BGP4 authenticate via MD5.
Switching: Network Resiliency and Forwarding Control
Layer 2+
For network resiliency, ExtremeXOS offers a choice between standard protocols and more advanced Layer 2+ protocols, optimized for faster resiliency, larger scaling and simpler operation.
Spanning Tree Protocol: ExtremeXOS supports IEEE 802.1D STP, 802.1w RSTP and 802.1s MSTP. In Extreme Multiple Instance STP mode, ExtremeXOS allows a port or VLAN to belong to multiple STP domains and therefore adds flexibility to STP network design, further increasing resiliency. The implementation is also compatible with PVST+ and IEEE 802.1Q.
Ethernet Automatic Protection Switching (EAPS, RFC 3619), invented by Extreme Networks, is designed to prevent loops in a ring topology running Layer 2 traffic. Its role is similar to STP, however it is able to rapidly converge when a link breaks, transparently to VoIP calls, independent of the number of switches in a ring. Timing will be sub 50 ms in most deployments.
Resiliency Features: the Virtual Router Redundancy Protocol (VRRP) enables a group of routers to function as a single virtual default gateway. Extreme Standby Router Protocol™ (ESRP) can be implemented at both Layers 2 and 3. ESRP tracks link connectivity, VLANs, learned routes and ping responses. ESRP can be used as an STP and VRRP substitute, providing simplicity via a single protocol for Layer 2 and Layer 3 redundancy. Multiple instances of ESRP in the same VLAN allow direct host attachment to standby switches.
Virtual Private LAN Services (VPLS, RFC 4762) are used for signaling and provisioning subscriber VLANs and vMANs over the IP network core. Extreme Networks VPLS implementation interoperates with EAPS, ESRP, and STP to provide a connectivity option for delivering fault-tolerant Layer 2 services over a Layer 3 network core.
To further harden the network resiliency protocols of ExtremeXOS, Extreme Link Status Monitoring (ELSM) protects the network and resiliency protocols from the effects of unidirectional links to protocols. For bandwidth scaling, link aggregation (static and dynamic via LACP) utilizes the bandwidth of multiple links. IGMP Snooping and Multicast VLAN Registration preserve network bandwidth by forwarding only to ports and to VLANs with subscribers from a single multicast VLAN. If desired, static IGMP membership allows the force-forwarding of traffic through the network for high subscription response, and filters provide control over transmitted content.
IPv4
ExtremeXOS also offers a set of Layer 3 switching features all geared to increasing control and management on very large networks. The switching software implements static routes, RIP, OSPFv2, IS-IS and BGP4 for External BGP (EBGP) and Internal BGP (IBGP).
ExtremeXOS fields a rich set of IP multicast routing protocols, including PIM Dense Mode (PIM/DM), PIM Sparse Mode (PIM/ SM) and PIM Source Specific Multicast (PIM-SSM), which work hand in hand with the built-in IGMPv1/v2/v3 support. Multicast source routes can be shared between sites using MSDP and MBGP, for example, to share sources of distance learning multicast streams in a university backbone network. IGMP v2/v3 SSM mapping allows both IGMPv2 and IGMPv3 in the network, upgrading to the more powerful and secure IGMPv3 where needed.
Designed for IPv6
IPv6 offers improved network intelligence and a considerable number of new capabilities over IPv4. However, there are specific challenges regarding whether to choose to actively participate in the transition to IPv6 or hold off to further evaluate. Extreme Networks has taken a ground-up approach to addressing these challenges by designing IPv6 intelligence into ExtremeXOS from the beginning.
Extreme Networks has designed an architecture for the performance, flexibility and security requirements of IPv6 without compromising operational simplicity (see Figure 5).
Features include Layer 2 and Layer 3 IPv6 forwarding, routing protocols and tunnels. ExtremeXOS provides investment protection and allows a safe and smooth transition by tunneling IPv6 traffic across non-IPv6-aware parts of the network.
ExtremeXOS platforms offer wire-speed ACLs – providing defense and control over the next generation of IP. Even when operating with IPv4, ExtremeXOS can harden the network to attacks using IPv6 transport.
In the Data Center and in the Central Office
Data Centers
Data center managers face unique challenges, such as virtual machine mobility and security. ExtremeXOS supports multiple capabilities and features to support this ever-evolving environment.
XNV (ExtremeXOS Network Virtualization) is a set of software modules for the ExtremeXOS-based switching product portfolio, and is available via the Data Center Feature Pack for Ridgeline, a network and service management application. XNV brings insight, control and automation for highly virtualized data centers to the network.
ExtremeXOS Direct Attach eliminates switching at the virtual switch layer, simplifying the network and improving performance. Direct Attach enables data center simplification by reducing network tiers from 4 or 5 tiers to just 3 or 2 tiers, depending on the size of the data center. Direct Attach is available through the Direct Attach Feature Pack for select Extreme Networks switches.
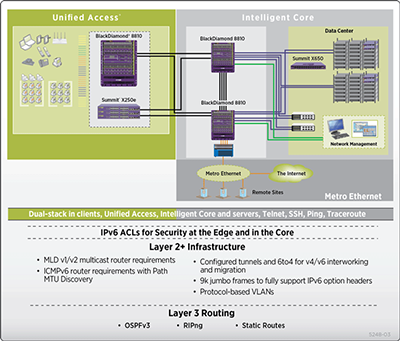 Figure 5: Edge-to-Core IPv6-Enabled Infrastructure
Figure 5: Edge-to-Core IPv6-Enabled Infrastructure
Priority-based Flow Control (PFC), or IEEE 802.1Qbb, allows network traffic to be controlled independently based on Class of Service. PFC allows network traffic that requires lossless throughput to be prioritized, while other traffic types that do not require or perform better without PFC can continue as normal.
Data Center Bridging eXchange (DCBX) [or IEEE 802.1Qaz [IEEE P802.1Qaz/D2.3, Virtual Bridged Local Area Networks – Amendment: Enhanced Transmission Selection for Bandwidth Sharing between Traffic Classes, December 17, 2010] is used by Data Center Bridging (DCB) devices to exchange configuration information with directly connected peers. The protocol can be used for configuring PFC, ETS, and application parameters on peers. The protocol can also be used to detect misconfiguration in peers.
Multi-Switch Link Aggregation Groups (M-LAG) can address bandwidth limitations and improve network resiliency, in part by routing network traffic around bottlenecks, reducing the risks of a single point of failure, and allowing load balancing across multiple switches.
Service-Provider Central Offices
Service providers and their central office facilities face unique challenges in serving thousands to hundreds of thousands of subscribers, often with multiple services, as well as residential, business Ethernet, and/or Ethernet mobile backhaul. ExtremeXOS includes multiple features and capabilities to support the rigorous demands of the carrier environment.
MPLS
MPLS and H-VPLS are supported on multiple ExtremeXOS-based switches through licensable software modules. MPLS (MultiProtocol Label Switching) can support multiple service offerings and models, and offers traffic engineering, traffic management and out-of-band control. H-VPLS (Hierarchical Virtual Private LAN Service) allows business Ethernet service offerings to be deployed across geographically dispersed locations using multi-tenant unit (MTU) switches.
Mobile Backhaul
With E4G cell site and cell site aggregation routers, ExtremeXOS is capable of providing carrier grade resiliency, synchronization and high performance Gigabit Ethernet switching for deploying true 4G mobile backhaul solutions.
ExtremeXOS-based switches supports two packet ring resiliency protocols, Ethernet Automatic Protection Switching (EAPS) RFC 3619 and ITU G.8032 standard for Ethernet Ring Protection Switching, to enable carrier grade resiliency for a superior subscriber experience and ensuring service level agreements.
ExtremeXOS is capable of providing Synchronous Ethernet through dedicated hardware support for ITU-T G.8262 Synchronous Ethernet (SyncE) and IEEE 1588v2 Precision Time Protocol. SyncE distributes the clock between nodes and provides the benefit of deterministic frequency distribution. IEEE 1588v2 uses timestamps to distribute both time and frequency between nodes. Synchronous Ethernet ensures that 2G/3G TDM traffic encapsulated in TDM pseudowires and other Ethernet traffic are synchronized over fiber or microwave connections to provide exceptional subscriber quality experience when hand-off occurs between cell towers as subscriber roams with their mobile devices.
Software Defined Networking Ready
ExtremeXOS based switches are SDN ready offering support for industry standard OpenFlow and OpenStack. ExtremeXOS implementation of OpenFlow is based on OpenFlow 1.0 APIs that allows an external OpenFlow based SDN controller to access and control the forwarding plane of the ExtremeXOS based network device. Thus ExtremeXOS based switches offers a programming interface through OpenFlow to enable high degree of automation in provisioning network services for many upper layer business critical applications that run on the OpenFlow based SDN controller.
ExtremeXOS based switches also allow for integration with the OpenStack open source cloud computing platform for public and private clouds through its Extreme Quantum plugin. The plugin provides a scalable, automated, rich API-driven system that enables networking-as-a-service model managing data center interconnect solutions and large multi-tenant networks.
Ethernet Audio Video Bridging
ExtremeXOS supports the latest IEEE 802.1 Audio Video Bridging (AVB) standards to enable reliable, real-time audio/video transmission over Ethernet for today’s high-definition and time-sensitive multimedia streams with perfect Quality of Service (QoS). The IEEE standards include:
- IEEE 802.1ak - Multiple Registration Protocol (MRP/MMRP)
- IEEE 802.1AS - Timing and Synchronization for Time Sensitive Applications in Bridged Local Area
- Networks (gPTP)
- IEEE 802.1Qat - Stream Reservation Protocol (SRP)
- IEEE 802.1Qav - Forwarding and Queuing Enhancements for Time-Sensitive Streams
IEEE 802.1BA Audio Video Bridging Systems
ExtremeXOS uses these AVB technologies to identify and reserve the network resources for AVB traffic streams and supports precise synchronous streaming capability for reliable and high quality audio/video transmission over Ethernet. The AVB protocols enables time sensitive multimedia streams to be sent over the Ethernet network with low latency and guarantees service quality for today’s real-time, high definition information and entertainment options.
Specifications:
| Switching | ||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| ExtremeXOS 15.6.1 Supported Protocols and Standards |
Summit X430 | Summit X440 | Summit X460 | Summit X460-G2 | Summit X480 | Summit X670 | Summit X670-G2 | Summit X770 | Black Diamond 8800 |
Black Diamond X8 |
EAG-200 | EAG-400 |
| IEEE 802.1D – 1998 Spanning Tree Protocol (STP) |
• | • | • | • | • | • | • | • | • | • | • | • |
| IEEE 802.1D – 2004 Spanning Tree Protocol (STP and RSTP) |
• | • | • | • | • | • | • | • | • | • | • | • |
| IEEE 802.1w – 2001 Rapid Reconfiguration for STP, RSTP |
• | • | • | • | • | • | • | • | • | • | • | • |
| IEEE 802.1Q – 2003 (formerly IEEE 802.1s) Multiple Instances of STP, MSTP |
• | • | • | • | • | • | • | • | • | • | • | • |
| EMISTP, Extreme Multiple Instances of Spanning Tree Protocol |
• | • | • | • | • | • | • | • | • | • | • | • |
| PVST+, Per VLAN STP (802.1Q interoperable) |
• | • | • | • | • | • | • | • | • | • | • | • |
| Draft-ietf-bridge-rstpmib-03.txt – Definitions of Managed Objects for Bridges with Rapid Spanning Tree Protocol |
• | • | • | • | • | • | • | • | • | • | • | • |
| Extreme Standby Router Protocol (ESRP) |
• | • | • | • | • | • | • | • | • | • | • | • |
| IEEE 802.1Q – 1998 Virtual Bridged Local Area Networks |
• | • | • | • | • | • | • | • | • | • | • | • |
| IEEE 802.3ad Static load sharing configuration and LACP based dynamic configuration |
• | • | • | • | • | • | • | • | • | • | • | • |
| Software Redundant Ports | • | • | • | • | • | • | • | • | • | • | • | • |
| Multi-Switch Link Aggregation Groups (M-LAG) |
- | • | • | • | • | • | • | • | • | • | • | • |
| IEEE 802.1AB – LLDP Link Layer Discovery Protocol |
• | • | • | • | • | • | • | • | • | • | • | • |
| LLDP Media Endpoint Discovery (LLDP-MED), ANSI/TIA-1057, draft 08 |
• | • | • | • | • | • | • | • | • | • | • | • |
| Extreme Discovery Protocol (EDP) |
• | • | • | • | • | • | • | • | • | • | • | • |
| Cisco Discovery Protocol (CDP) v1 |
• | • | • | • | • | • | • | • | • | • | • | • |
| Extreme Loop Recovery Protocol (ELRP) |
• | • | • | • | • | • | • | • | • | • | • | • |
| Extreme Link State Monitoring (ELSM) |
• | • | • | • | • | • | • | • | • | • | • | • |
| IEEE 802.1ag L2 Ping and traceroute, Connectivity Fault Management |
• | • | • | • | • | • | • | • | • | • | • | • |
| ITU-T Y.1731 Frame delay measurements |
• | • | • | • | • | • | • | • | • | • | • | • |
| ITU-T Y.1731 Frame Delay |
• | • | • | • | • | • | • | • | • | • | • | • |
| ITU-T Y.1731 Frame Loss |
- | - | • | • | • | • | • | • | • | • | • | • |
| IEEE 802.3ah Ethernet OAM – Unidirectional Link Fault Management |
- | - | • | • | - | • | • | - | - | - | • | • |
| RFC 3619 Ethernet Automatic Protection Switching (EAPS) Version 1 and Version 2 |
• | • | • | • | • | • | • | • | • | • | • | • |
| ITU G.8032 Ethernet Ring Protection Switching |
• | • | • | • | • | • | • | • | • | • | • | • |
| IEEE 802.1 Audio Video Bridging (AVB) standards |
AV | AV | AV | AV | - | AV | AV | AV | - | - | - | - |
| OpenFlow Protocol 1.0 | - | OF | OF | OF | OF | OF | OF | OF | - | - | - | - |
Please view datasheet for full list of specifications.
Documentation:
Download the Extreme Networks ExtremXOS Operating System Datasheet (.PDF)

