
Extreme NetworksExtreme Defender for IoT
Secure Connections for IoT Devices that Lack Embedded Security
Click here to jump to more pricing!
Overview:
Securing Devices with Extreme Defender for IoT
Extreme Defender for IoT is a unique, award-winning solution, that delivers security for end points which have limited or even no embedded security capabilities. It is especially targeted to aging wired devices, that need to roam around a room, a building or even a campus.
It complement s a customer's existing securit y infrastructure by adding in-line defense directly at the IoT device it self. And it can be deployed over any network infrastructure to enable secure IoT management without significant network changes.
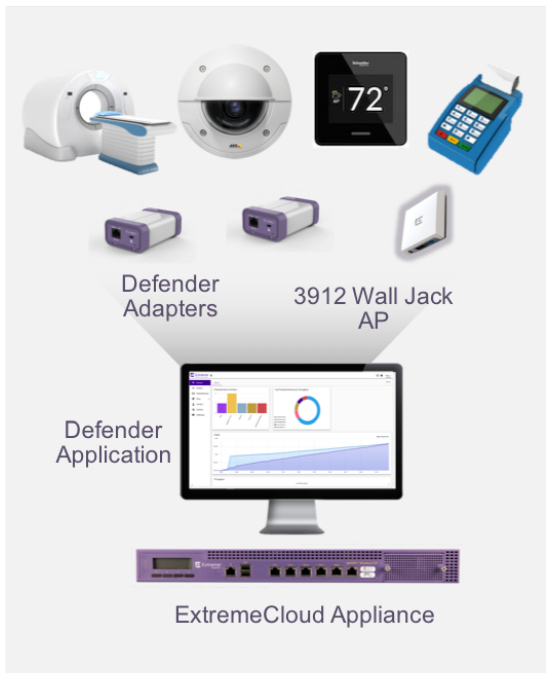
Extreme Defender Components
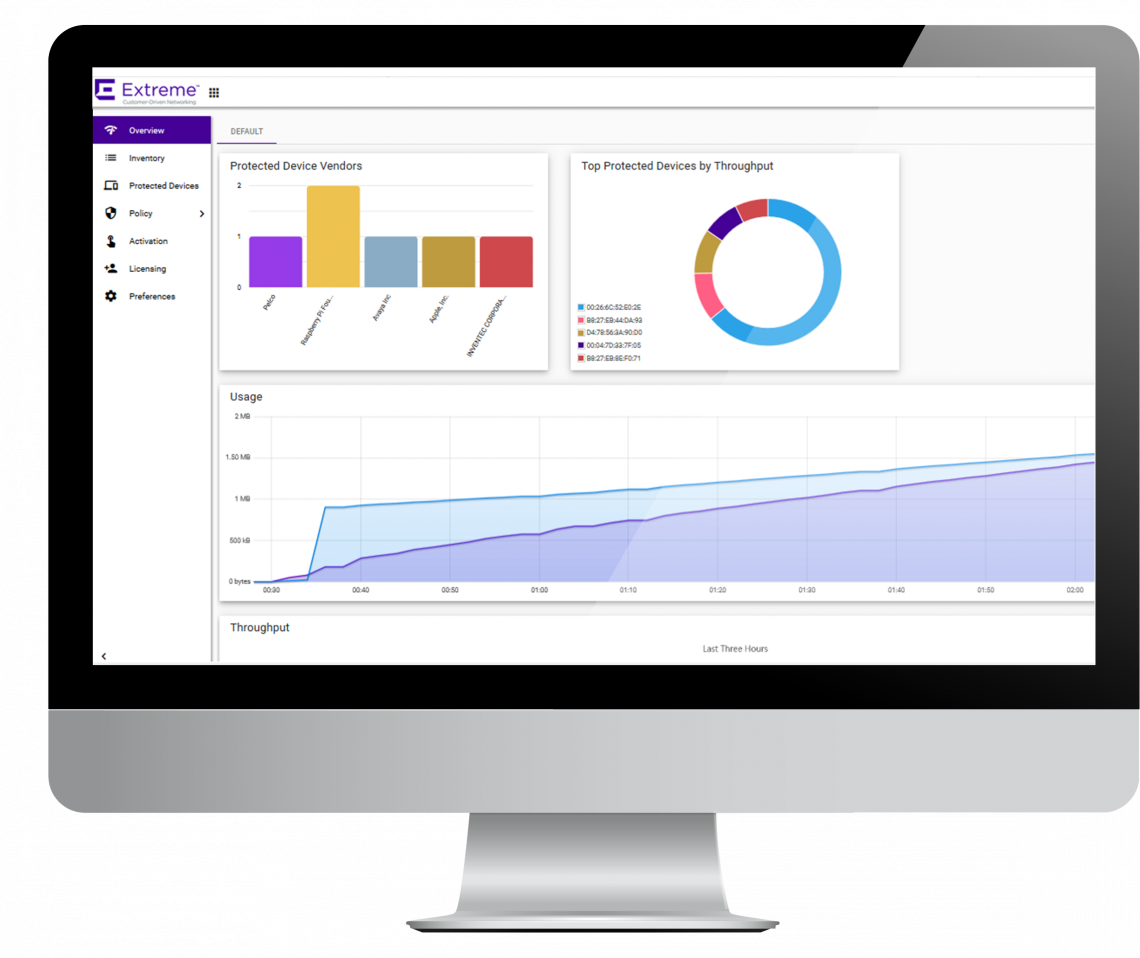
Defender Application: A user friendly application that enables the centralized creation of security profiles for groups of IoT devices. Once profiles are created, non-technical staff can securely on-board and move their devices. They can also monitor and track their asset s through intuitive dashboards and centralized inventory.
Defender Adapter (SA201) and the ExtremeWireless Indoor Access PointProvides a proxy service for the Defender application to both manage and secure IoT devices. Their specific role is to monitor traffic flows - with full Layer 2 to 7 visibility - to ensure that the device is operating according to it s expected behavior. The Defender Adapter is a single port device that sits between the network and the IoT device providing in-line defense
ExtremeCloud Appliance: Available as a hardware based or virtual-appliance, the ExtremeCloud Appliance, is a premise-based solution that provides cloud-like management and controller functionality for Extreme Smart OmniEdge (wired and wireless) solutions. With a full suite of rich APIs to customize applications, it is the supported platform for the Defender Application.
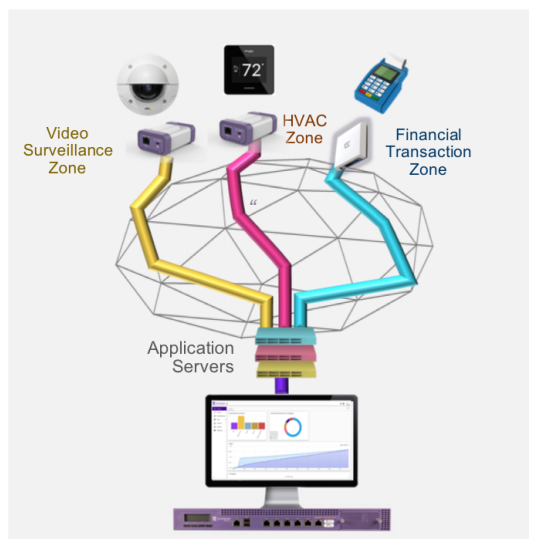
Secure Zones with Fabric Connect
Extreme Defender is optimized for use with Extreme Fabric Connect, Extreme's Campus Fabric solution. One of the main benefit s of Fabric Connect is it s ability to quickly and easily create secure zones at scale. Rather than complex configuration, these secure zones can be deployed very quickly and easily at the network edges. In addition, on a Fabric Connect infrastructure, an auto-attach protocol called Fabric Attach is supported on the Defender Adapter and the Access Point. This enables dynamic automatic attachment of end point s as well as full network service automation so that the end to end secure zone is created dynamically as the device is on-boarded.
Features:
How Defender Secures Devices
Applies profiles directly at the IoT device, ensuring the device operates expectedly
Controls IoT device attachment and access to the network
Isolates groups of IoT devices into secure zones or network segments
Secures your critical IoT devices
Applies and enforces device profiles, controls IoT device network access. Isolates IoT devices into secure zones.
Secure zones at scale
Works with Fabric Connect to create secure zones that can be deployed quickly and easily at the network edge. Or works over 3rd party networks isolating groups of devices in IPsec tunnels.
Simple User Interface
Enable non-technical staff to securely on-board, monitor, track and move their devices without burdening already taxed networking and IT teams.
Documentation:
Download the Extreme Defender for IoT Solution Brief (.PDF)
Download the Extreme Defender Adapter Datasheet (.PDF)
Our Price: $749.00

